The bio-computer interNET . . . .the North Pole magNETic field .... Benjamin NETanyahu - - - -> NET WAR to control MariNETte, Wisconsin - - > Boy Scout messenger Sam Hengel warns world of the NET wars.
RD-blog-1518
Boy scout Sam Hengel sacrificed his life to help save the world. His obvious SIGNAL is very important .....and has been deliberately ignorded by citizens, governments, and universities.
Even his own group, the BOY SCOUTS of America have betrayed their pledge to the United States of America. Sam Hengel and his subliminal mind intercepted various CARL JUNG collective unconsciousness signals and correctly interpreted the signals .... that there something very wrong ....... that major subconscious wars are going on ..... the deep down atomic brain ... social psychology SCIENCE WARS.
The brave intellectual spirit of Sam Hengel stepped up and defended Nature and the Central Nervous System 370 abstract brain symbolic computer from attack. His bravery .....and his tragedy sent an important cryptographic SIGNAL ....... that eventually was figured out by a serious thinker. But who else cares? Citizens could care less about anything ...they will not help understand the many facets of the social SCIENCE wars and the neuroscience secret language wars of society.
Sam Hengel, Marinette High School student who held classroom ...Nov 30, 2010 – Sam Hengel, Marinette High School student who held classroom hostage, ...
A Wisconsin teen
who held 23 students and a teacher hostage at ...
who held 23 students
who held 23 students
who held 23 students
who held 23 students
Adult BOY SCOUTS and former Boy Scouts are to intellectully lazy to even try to understand the situation. Instead they diminish
the 23 chromosome HERO
of the genetic wars --> Sam Hengel.
Cryptography - Wikipedia, the free encyclopedia
Cryptography - Dec 16, 2011 – the study of transforming information in order to make it secure from unintended recipients or use.
A review of cryptography protocols, algorithms, and design.
Cryptography www.crypto-class.org/Cached
Cryptography www.crypto-class.org/Cached
Cryptography www.crypto-class.org/Cached
Cryptography
crypto-class.org/Cached
crypto-class.org/Cached
cry + pto + class --> Cry point circle class
cry pto-class --> point at Steven K. at NIU, Cole Hall
cry pto-class --> point at Mr.CHO, Virginia Tech
cry pto-class --> point at Major NH - Fort Hood amino acids
cry pto-class --> point at Sam Hengel gentics warrior
Cryptography is an indispensable tool for protecting information in bio-computer chromosome/ brain systems. This course explains the inner workings of cryptographic primitives and
23 Chromosomes --> Base 2 math power 3 = 8 data bits ....
secrets of chromosome life ..picture below
Bio-computer -->cryptography protocols, algorithms, and design.
Thus Sam Hengel was protecting his biology system from the the Internet BLOG war that is in process. The English language word BIOLOGY describes our mathematical-life ...specifically our high school algebra logarithms .....the mantissa and characteristic.
In the modern world, Darwinian evolutions of symbolic life involves our human data processing system. We are symbolic machines. These math components of bio-computer life are very important. The interNET communications systems has many good features and many abused features ..especially the usage of the interNET for excessive nonsense.
The copper wire INternet systems is an external system ...and is a partial mirror/ a reflection of our internal systems ..... collective unconsciousness, data stream of consciousness, schools of thought, States of MIND, etc. Dozens of different formats have been described in the last 400 years in literature ...... and in the last 100 years with social pscychology theories and books.
Humans are biological computers.....have been for thousands of years. Now, we are biological symbolic processors. We receive input data into our eyes and ears ..... and other sources of data ..touch, smell, etc. The brain computer has to look at this input data ..... make decisons, etc.
.
BIOLOGY --> Bio + Log y (see math book of life)
BIOLOGY algebraic subset letters are
B..LOG --> Base Logarithms .......
Thus the copper wire/wireless INTERNET system
uses the WEB and BLOG format to allow humans
and their subconscious MIND to engage in REAL symbolic battles with other humans and their subconscious MINDS ......VIA the system.
Before the Internet, some television talk shows and radio talk shows engaged in Central Nervous System debates at the surface level ....... the data received by the listening audience was routed to their subliminal minds ...... and such a mind could mis-interpret the data.
Today, we have really have a battle of Central Nervous Systems using data streams comprised of nouns, verbs, concepts, math equations, some pictures/graphics, etc. Thus the increase in university and high shootings in the last ten years; because the school systems are on such an ego trip ...they refuse to look at the ERRORS that independent researchers notice.
Northern Illinois University, Virginia Tech, and other universities have reached the epitome of arrogance ..... ignoring the empirical data of their tragedies. Irresponsible snobs that refuse to communicate properly and in a diplomatic fashion .... ought not be in charge of knowledge. Those school will not to help understand the deeper CAUSE behind the tragic EFFECT.
Some networks and data signals that exist in the modern world are listed below.
They are concepts .....that you have to think about. You have to complete the picture with an more explainable answer. Thus challenged ..... will you be an intellecual chicken?
The situation is more involved, but this is a good starting point.
All these symbolic components are directly or indirectly can be inside the human brain.
C.P. Snow clearly stated that " Two Cultures" existed.
The book " Tale of Two Cities" reflected the same observation.
What are the 23 chromsome... biochemistry WAR secrets of Marinette?
DNA nucleotide zip code with 43 --> 4 exponent 3 = 64 codons.
Nucleic Acids to Amino Acids: DNA Specifies Protein |
Learn ...www.nature.com/.../
by A Smith - 2008 - Related articles
How can the four bases that make up DNA specify the 20 amino acids that ... It was also known that there are only four nucleotides in mRNA: adenine (A), ... However, a triplet code produces 64 (43 = 64) possible combinations, or codons. Thus ...
The Information in DNA Determines Cellular Function via
The three-letter nature of codons means that the four nucleotides found in mRNA — A, U, G, and C — can produce a total of 64 different combinations. Of these ...
Piercing the corporate veil - Wikipedia,
Jump to Criminal lawý: In English criminal law there have been cases in which the courts ... received by a company have been regarded as having been 'obtained' by ... A court can " pierce" the carapace of the corporate entity and look at ...
Basis for limited liability - Germany - United Kingdom - United States
Piercing the Corporate Veil legal definition of Piercing the Corporate
What does Piercing the Corporate Veil mean in law? ... The corporation today remains the most common form of business organization because, theoretically, ...
Business Law - What does it mean to pierce the corporate veil?
In doing so, the creditor is asking the court to pierce the corporate veil and make the business owners personally liable for the debts, liabilities and obligations of ...
Piercing the Corporate Veil
QuickMBA / Business Law / Corporate Veil ... A court may pierce through the veil of liability protection if the corporation does not follow proper corporate ...
Piercing the Corporate Veil | Citizen Media Law Project
Jul 6, 2010 – Piercing the Corporate Veil. A properly formed and operated corporation or LLC offers its owners limited liability for the debts of the business, ...
Thus we have a biology communications war ...with many facets. It needs to be understood.
Maybe, someday, cities will face REALITY and help understand how EARTH LAB works and affects our daily LIFE or DEATH.
NATURE decides who will represent the atomic social anthropology component of the Hierarchy Problem of physics. FermiLAB can't communicate, University of Chicago and other universities can't handle the simple process of communications; thus Darwinian atomic selection will decide whose human brain electron circuits has the electron node .... capable of working as a communications node.
The reader may just glance at the concepts below ..to be aware that they exist.
Please be aware that bio-computer systems have existed..... such as the ancient Roman empire ...was really built by bio-computers using the human processor.
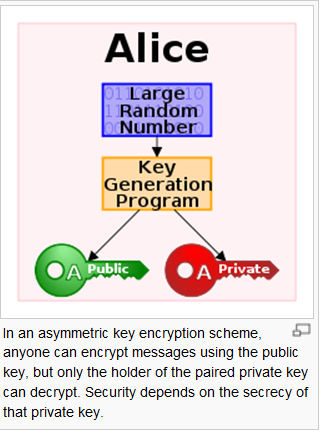
Below, we see --> keys, one to lock or encrypt the
Thus you see that a few events, with incomplete explanation in newspapers.
--> Sam Hengel was involved in bio-computer battle .
--> The Penn State locker room molestation issue ....
is a cover-up by Penn State administration to allow their computer science departments and biology departments to tryto control the human bio-computer system ..... a major political power scheme ....to manipulate the human mind. Thus Penn State uses the decoy strategy of blaming Sandusky ...while the real lock error issue is ignored.
Washington, DC funds this type of project ...on the theory they will end up on top of the society pyramid. Nature has other ideas ...... and subset humans and their subset institutions are small potatoes compared to Nature's vast intellect and social VECTOR forces.
--> Virginia TECH secret voodoo tricks failed.
They tried to attack Nature's ENcrypt process .....hence
ENcrypt --> En + Cry + pt -->
English shooting + cry for dead students + point finger at Mr.CHO as soley responsible for the EVENT. The biggest line of BS ever invented in modern society ..... lies about the deeper CAUSES of the EVENT. Thus the LIES/schemes of Virginia ....... spread to Europe at nthe BATTLE of LIES at Liege, Belgium.
.
.
.
.
.
.
.
From the internet -->
Public-key cryptography refers to a cryptographic system requiring two separate keys, one to lock or encrypt the plaintext, and one to unlock or decrypt the cyphertext. Neither key will do both functions. One of these keys is published or public and the other is kept private. If the lock/encryption key is the one published then the system enables private communication from the public to the unlocking key's owner. If the unlock/decryption key is the one published then the system serves as a signature verifier of documents locked by the owner of the private key. Although in this latter case, since encrypting the entire message is relatively expensive computationally, in practice just a hash of the message is encrypted for signature verification purposes.
This cryptographic approach uses asymmetric key algorithms such as RSA, hence the more general name of "asymmetric key cryptography". Some of these algorithms have the public key/private key property; that is, neither key is derivable from knowledge of the other; not all asymmetric key algorithms do. Those with this property are particularly useful and have been widely deployed, and are the source of the commonly used name. The public key is used to transform a message into an unreadable form, decryptable only by using the (different but matching) private key. Participants in such a system must create a mathematically linked key pair (i.e., a public and a private key). By publishing the public key, the key producer empowers anyone who gets a copy of the public key to produce messages only s/he can read -- because only the key producer has a copy of the private key (required for decryption). When someone wants to send a secure message to the creator of those keys, the sender encrypts it (i.e., transforms it into an unreadable form) using the intended recipient's public key; to decrypt the message, the recipient uses the private key. No one else, including the sender, can do so.
How it worksThe distinguishing technique used in public key cryptography is the use of asymmetric key algorithms, where the key used to encrypt a message is not the same as the key used to decrypt it. Each user has a pair of cryptographic keys — a public encryption key and a private decryption key. The publicly available encrypting-key is widely distributed, while the private decrypting-key is known only to the recipient. Messages are encrypted with the recipient's public key and can be decrypted only with the corresponding private key. The keys are related mathematically, but parameters are chosen so that determining the private key from the public key is prohibitively expensive. The discovery of algorithms that could produce public/private key pairs revolutionized the practice of cryptography beginning in the mid-1970s.
In contrast, symmetric-key algorithms, variations of which having been used for thousands of years, use a single secret key — which must be shared and kept private by both sender and receiver — for both encryption and decryption. To use a symmetric encryption scheme, the sender and receiver must securely share a key in advance.
Because symmetric key algorithms are nearly always much less computationally intensive, it is common to exchange a key using a key-exchange algorithm and transmit data using that key and a symmetric key algorithm. PGP and the SSL/TLS family of schemes do this, for instance, and are thus called hybrid cryptosystems.
Thus we see CLUES to a puzzle regarding the BOY SCOUTS, FFA (Matt Anderson), 4-H Club and many other organizations in the United States AND their failure to understand simple concepts ...regarding Margaret Mead atomic nuclear family laws ....that is atomic social anthropology and atomic social philosophy. While these organizations are very good ..for the most part; they assume that they are superior to the laws of Nature and the 23 chromosome laws of Nature.
Thus we Nature's Darwinian selection of special agent Sam Hengel....
address 2139 Pierce Avenue.......MISSION
penetrate--> Pierce the Corporate Veil ...message
for agent--> Pier director of FermiLAB physics
and the IRON CUTRAIN problem of the
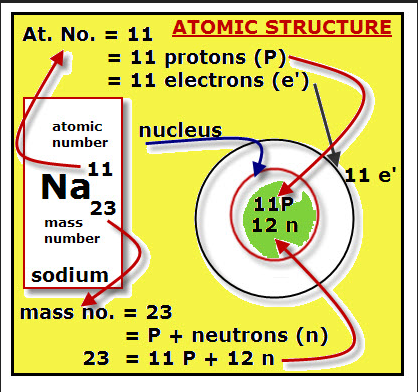
Fe = Ferrous Oxide atom and iron Hemoglobin protein thought ERRORS
at the Department of Energy and
the Fe = Federal government intellectual violations of Fe = 26 protons of Ferrous oxide atomic rules for human li.FE --> Margaret Mead atomic nuclear family LIFE VIA the periodic atomic table elements and their extension to humanoid expression FORMAT.
.
Sam Hengel, Marinette High School student who held classroom ...Nov 30, 2010 – Sam Hengel, Marinette High School student who held classroom hostage, ...
A Wisconsin teen
who held 23 students and a teacher hostage at ...
who held 23 students
who held 23 students
who held 23 students
who held 23 students FermilAB physics science Wars
Brain Science WAR signal Na --> North america -->
phonetics SOUND equivalent ( Sodium --> So dumb )
Thus Nature send subset humans a SRP signal .....for the
molecuar cell biology SRP = Signal Recognition Particle.
Apparently this brain particle is missing in hundreds of millions of students and parents.
As Nature says 'If you don't use it ...you lose it" ....symbolic knowledge is modern food for thought. That is serious knowledge.. basic algebra, genetics, basic biochemsitry, etc.
We not talking rocket science .....we are talking some simple concepts ..like number 23 .....sends a message about the Margaret Mead atomic social science war with the Office of Science and DARPA and
the secret BRAVE NEW WORLD projects.
.
.
Thus we see the Margaret Mead atomic nuclear family signal .....
.......23 students held hostage --> 238 decay of human atomic brain.
Special BOY SCOUT undercover agent Sam Hengel ....
grammer emmitter messages of the event .... agent for
gamma information emmitters (Project atomic navigation )
SAM Hengel ...age 15 .. Gama ....map of the elements of atomic society life.
Vasco da Gama - The Portuguese navigator Vasco da Gama led an expedition at the end of the 15th century that opened the sea route to India by way of the Cape of Good Hope ...
-- the Portuguese BOY Scout navigator ..... from .......
Sam Hengel - EagleHerald Marinette & Menominee online ...
Dec 3, 2010 - He has been raised in Porterfield, Wis. and attended Marinette High School as a Sophomore. Sam was a proud member of the Boy Scouts of ....
-- the end of the 15th --> end of life age 15
-- that opened the sea route --> open the see route
-- to India --> to find intellectual america
by way of the Cape of Good Hope ...
-- the Maragret Mead atomic nuclear family hostage code 238 VIA code 23 HOSTAGES in Marinette
Thus SAM Hengel --> Message to Uncle SAM ..... from SAMPLE space ...that is the
mathematical-physics dimensions of the United States.
Introduction to M-theory - Wikipedia, the free
In non-technical terms, M-theory presents an idea about the basic substance of ... This was later increased to 11 dimensions based on various interpretations of ...
Background - Status - See also - References
M-theory - Wikipedia,
In theoretical physics, M-theory is an extension of string theory in which 11 dimensions are identified. Because the dimensionality exceeds that of superstring ...
M-theory applications and 11 dimensions
- Marinette theory of SKU 11. Thus a typical city that doen't pay attention to knowledge except pizza and sports. Do chromosomes exist? Is a football field part of Einstein's data field theory?
Why is the English class sentence -->
Twenty - four hours = 24 hours a day .....
math says 20 - 4 hours = 16 hours per day
M-theory physics war report ignored by newspapers
- Manhattan theory and 11-dimensions battle of Sept 11, 2001
Maybe some people will like to help think about these puzzles.
Some CLUES are mentioned above... provide a partial outline.
CONTACT: Principle science researcher HERB ZINSER
Mail Address: P.O.BOX 134, Watertown, WI 53094-0134, USA
E-Mail: Herb@Zinoproject.com
Website: www.zinoproject.com
No feedback yet
Additional Posts
- Computer Earth system 370 biochemistry WAR with alien subroutines used by business, cities, universities, and other groups. What is your brain computer death code?
- The bio-computer interNET . . . .the North Pole magNETic field .... Benjamin NETanyahu - - - -> NET WAR to control MariNETte, Wisconsin - - > Boy Scout messenger Sam Hengel warns world of the NET wars.
- Earth Lab study of Pentagon brain neurotransmitter problem and the 64 codons of DNA nucleotide problem
- Ancient European neurotransmitters PLOT to destroy United States smoke-stack industry. Norway , Little Norway, and the Netherlands promote the secret WAR languages. Cause: university communications errors --> Effect: Utoeya
- The Niels Bohr Institute of Copenhagen, Denmark and the EARTH LAB atomic anthropology experiments in the city of Madison with the University of Wisconsin